Traditional federal security solutions tend to focus on infrastructure, but overlook the employee or contractor. This can create a blind spot for your agency, preventing you from knowing what data users are accessing and what they’re doing with it. This security void, combined with increasingly open networks among agencies, contractors and programs, leaves your sensitive data vulnerable.
Visibility to Instantly Detect Suspicious User Behavior
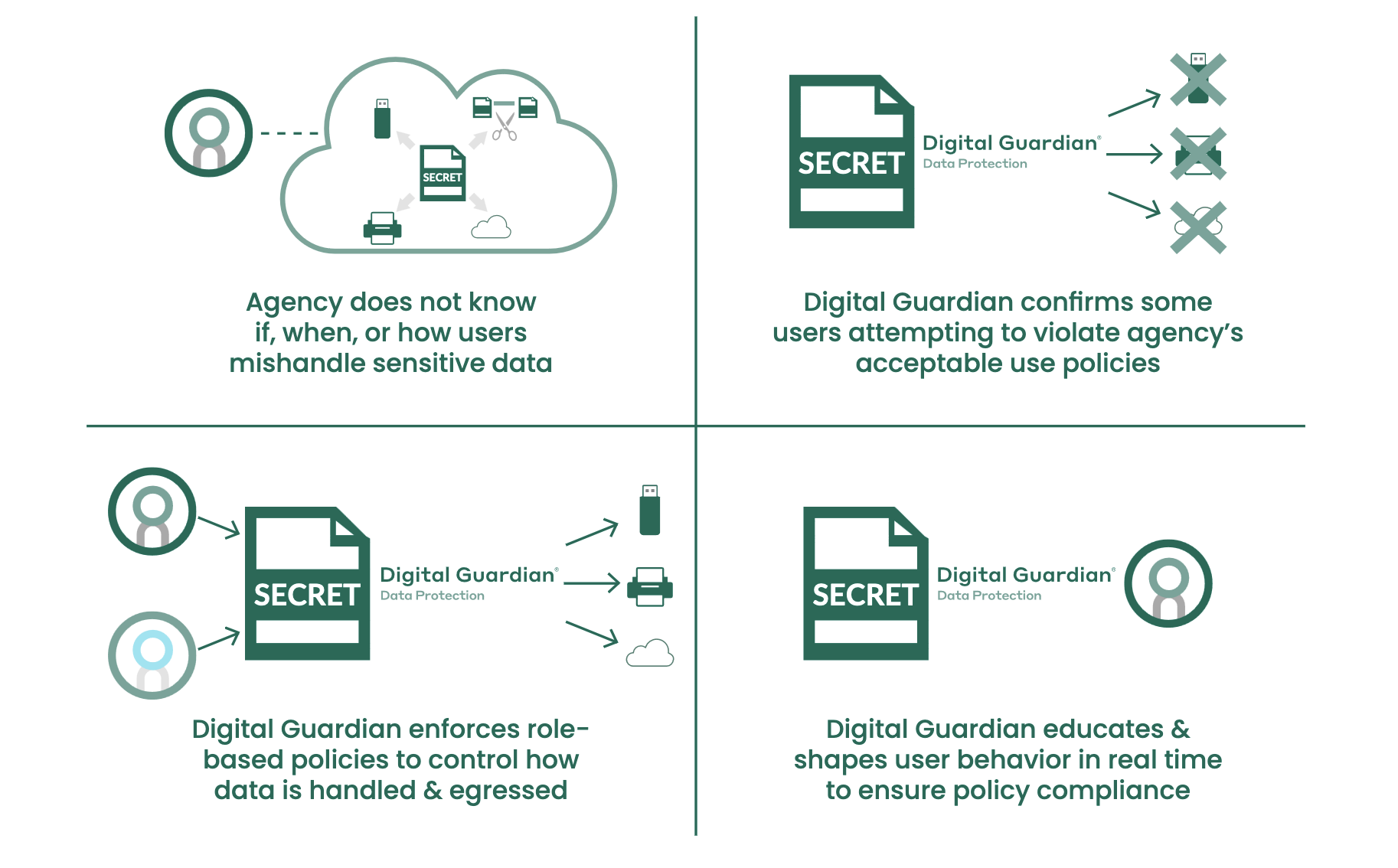
Digital Guardian User Activity Monitoring offers complete user visibility and control regardless of what users are running, what they’re running it on, and whether or not they’re on the network. Your agency can audit, monitor, limit and report on all end-user activity in real-time, and also perform investigative tasks.
MANY GOVERNMENT WORKERS DON’T CONSIDER SECURITY WHEN SHARING WITH THIRD PARTIES
31% of government workers said they never or only occasionally consider data security or privacy issues into account when they share information with vendors or other external stakeholders.
- Wall Street Journal, Survey: Many Government Employees Use Personal Email for Work
Our solution helps government pros classify, categorize and tag data so every action is tracked and accounted for – providing a detailed audit trail that can aid investigations and help your agency show compliance with mandates like Insider Threat Executive Order 13587. Whether it’s deployed on premise or as a cloud based managed service, Digital Guardian begins to work as soon as it’s installed, enabling instant detection, investigation and containment of suspicious activity.
Implementation is greatly simplified… with average deployment times much shorter than other DLP products. It can often be completed in a single day, with only minimal policy tuning required thereafter.
Source - Data Loss Prevention Leading Vendors Review, DLP Experts
User Activity Monitoring in Action
KEY BENEFITS
CONTINUOUSLY RECORD EVERY USER ACTION WITH SENSITIVE DATA
- Track every system, data, application, and network event for each user
- Detect abnormal file operations or unauthorized attempts to exfiltrate
- Establish malicious intent by analyzing suspect actions in complete context
IDENTIFY SUSPICIOUS USER BEHAVIORS THAT DEVIATE FROM NORMAL DATA USE
- Establish user trends to baseline normal behavior and block/ prompt/alert extreme exceptions
- Identify suspicious/unauthorized applications used to access data
- Detect suspicious system configuration changes; alert when users deviate from normal activity
MONITOR, RECORD AND CONTROL TRUSTED USERS HANDLING SENSITIVE DATA
- Identify privileged users and control their use of sensitive data
- Prevent nonessential file access and operations by administrators
- Detect and investigate anomalous user behavior
- Prevent tampering with or circumventing policy controls
INVESTIGATE SUSPICIOUS BEHAVIOR AND PROVE MALICIOUS INTENT
- Collect and preserve chain-of-custody forensic evidence including capture files, screenshots and keystrokes
- Reconstruct incidents in their full context
MANAGE EVIDENCE FOR ACTIVE INVESTIGATIONS WITH ROLE-BASED CONTROLS
- Store evidence within a secured repository in the management console
- Collect and preserve forensics from target systems without physically securing the device
- Allow investigators to analyze evidence with elevated privileges